- Tuesday
- April 22nd, 2025
- Share Files

Get Complete Project Material File(s) Now! » Higher categories as globular algebras In this section, we recall and extend the setting for globular algebraic higher categories introduced by Batanin in [Bat98a]. In this setting, a particular theory of :-categories is...

Get Complete Project Material File(s) Now! » Active Learning and Version Space Algorithms In this first section, we provide an overview of the active learning domain and, in particular, version space techniques. Active Learning Settles [2012] and Monarch [2021] provide...

Get Complete Project Material File(s) Now! » Euclidian geometries for update rules Here, we introduce the elements that will be needed in the main proofs of our theorems Theorems 2.5.1 and 2.6.1; their articulation towards convex update rules mostly originates...
Get Complete Project Material File(s) Now! » One parameter persistence One-parameter persistence is the persistence theory associated to the poset (P; ) = (R; ). Hence, a one-parameter persistence module is an object of Pers(kR). The main example of one-parameter...

Get Complete Project Material File(s) Now! » System Overview and Background In this chapter, we review our design of an active learning-based explore-by-example system, present the essential background on data exploration, explore-by-example, active learning, and label-noise learning, and introduce a...
Get Complete Project Material File(s) Now! » Types of RNA RNA molecules are single stranded nucleic acids consisting of nucleotides adenine (A), guanine (G), cytosine (C) and uracil (U). Each nucleotide contains three components: a nitrogenous base, a five-carbon sugar...

Get Complete Project Material File(s) Now! » RDF Schema and entailment A valuable feature of RDF is RDF Schema (RDFS) that allows enhancing the descrip-tions in RDF graphs. RDFS triples declare semantic constraints between the classes and the properties used...

Get Complete Project Material File(s) Now! » Outsourced data Confidentiality by Encryption Despite that traditional encryption mechanisms (e.g., Data Encryption Standard (DES) [NIST 1999] and Advanced Encryption Standard (AES) [FIPS. 2001]) ensures strong confidentiality guarantees. They are suffering from two...
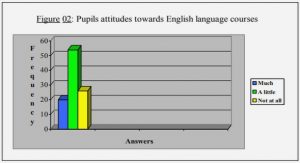
Get Complete Project Material File(s) Now! » Association in neural networks The operation of association involves the linkage of two or more pieces of information. An associative memory takes some “keys” as inputs and returns some “associated pattern” as the...

