- Tuesday
- July 23rd, 2024
- Share Files

Get Complete Project Material File(s) Now! » The importance of flourishing in everyday life The world flourish originally comes from the Latin word flor (flower) and is synonymous to growth and development (Hefferon, 2013). The concept of flourishing defines «...
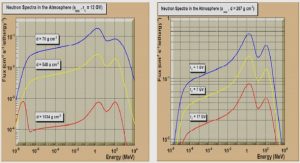
Get Complete Project Material File(s) Now! » Perspectives: Bridging Parallel Architectures and Software Parallelism You talk when you cease to be at peace with your thoughts. Kahlil Gibran “Anyone can build a fast CPU. The trick is to build a...

Get Complete Project Material File(s) Now! » Formal Security Proofs and Studies During my thesis, my main concern has been: how to unify and understand the link betwee the dierent metrics used to evaluate the sensitive information leakage of cryptographic...

Get Complete Project Material File(s) Now! » Public Phone Cards, the First Mass Market From 1978 to 1983, the French Direction Générale des Télécommunications1 (Directorate-General for Telecommunications) developed the principle of chip cards as payment cards for public phones in...

Get Complete Project Material File(s) Now! » Software Engineering The software engineering discipline is vast and promotes concepts to properly manage software development from its early existence. The field has developed over time several techniques and methodologies to produce software...

Get Complete Project Material File(s) Now! » Passive Source Localization using Acoustic Sensor Arrays The class of passive source localization estimators based on the measurements of an acoustic sensor array, can be roughly subcategorized into direct and indirect methods. The...
Get Complete Project Material File(s) Now! » Asset protection and data security Asset protection is a set of preventive techniques generally based on cryptographic primitives whose goal is to protect confidentiality and integrity and authenticity of data assets, software assets,...

Get Complete Project Material File(s) Now! » Recommender Systems Function In one hand, recommender systems are expected to suggest useful items to users by supporting them in various decision-making processes, such as what items to buy, what news to read,...

Get Complete Project Material File(s) Now! » Intrusion Detection in Wireless Mesh Networks The current IDS tools for wired networks cannot be directly applied to WMNs. Building IDS for inspecting the mesh network activity is not an easy task because...

