- Wednesday
- October 2nd, 2024
- Share Files
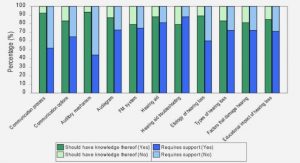
Get Complete Project Material File(s) Now! » Signature Based Detection (SBD) The static analysis enables a signature-based code classification. For example, if a malicious piece of code is found within the executable, an antivirus will drop the complete package. Nevertheless,...

Get Complete Project Material File(s) Now! » Next-Generation Wireless Networks The main driver of the evolution of wireless systems in the past was the need for higher data rates. However, with the proliferation of novel IoT applications, the key requirements...

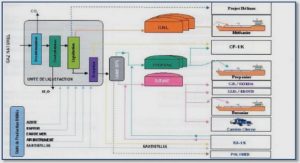
Get Complete Project Material File(s) Now! » Fukushima Daiichi Nuclear Accident On March 11, 2011, the Great East Japan Earthquake occurred [8]. The amplitude of the main shock was 9.0 and lasted two minutes. At the Fukushima Daiichi Nuclear Power...

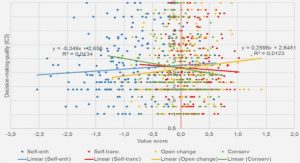
Get Complete Project Material File(s) Now! » Load Estimation in presence of a White Gaussian Noise We assume now that the channel is affected by a White Gaussian Noise. In order to analyze the noise effect on the accuracy of...
Get Complete Project Material File(s) Now! » IEEE 802.11 basics and evolution toward the IEEE 802.11ac amendment The first IEEE 802.11 [2] standard was launched in 1997, specifying a lot of notions related to wireless transmissions. It defines three PHY...

Get Complete Project Material File(s) Now! » Computationally hard problems Protocols in cryptography rely on computationally hard problems, i.e. problems that are assumed not to be solvable efficiently by a computer unless the under-lying secret is known. This is crucial...

Get Complete Project Material File(s) Now! » Maximum-Likelihood detection At the receiver side, the mission is to detect the transmitted vector from the received signal. The optimal detector which minimizes the probability of detection error is ruled by the ML...

Get Complete Project Material File(s) Now! » Cooperative Diversity in Virtual MIMO Systems If MIMO technology provides such significant performance gains, due to cost, complexity or other constraints the deployment of multiple antennas at user terminals in a network can...
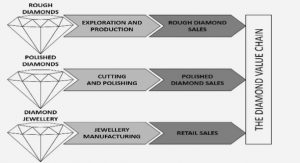
Get Complete Project Material File(s) Now! » NON-ORTHOGONAL MULTIPLE ACCESS (NOMA) The 4G network has seen considerable growth because of the distributions of the pro-fatable LTE networks worldwide. The need to develop next generation communication system such as the 5G...